While CyberLink PowerDirector 18 or newer can handle HEVC/H.265 files, it has a habit of crashing when ingesting HEVC files produced by Go Pro and other recording systems.
Continue reading “Go Pro HEVC and CyberLink PowerDirector”Native IPv6 with OpenBSD and Aussie Broadband
We are coming on two decades since IPv6 became a recognised standard and generally available but it is still not being widely adopted by people and organisations that have easy access to IPv4 address space. Even if you have a native IPv4 address, it will typically be in the form of some CG-NAT or other NAT on your customer premises equipment (CPE).
Things work so much better when they have a dedicated, routable IP address, especially when they don’t need to share a state table with other connections.
Continue reading “Native IPv6 with OpenBSD and Aussie Broadband”LibreSpeed on FreeBSD
I needed a mobile speed test server for my network diagnostics laptop recently. I have been using LibreSpeed in the office for quite some time so along with iperf3 on the same laptop, it was the logical choice.
Continue reading “LibreSpeed on FreeBSD”freebsd-update 13.0 caveats
By: Jason Tubnor @tubsta
We have been performing some extensive and edge case updates from FreeBSD versions earlier than 13.0. While in most cases, there have been no issues and most users will have a smooth upgrade process when we finally have 13.0-RELEASE hit but there are some issues that we hit which will need a bit of clarification and some advice on how to work them.
Continue reading “freebsd-update 13.0 caveats”Upgrading to FreeBSD 13.0
By: Jason Tubnor @tubsta
An email hit the freebsd-stable mail list the other day that reminded me with the upcoming release of FreeBSD 13 that includes OpenZFS 2.0, there is a bit of housekeeping that is required post upgrade, especially if you want to take advantage of the new zpool(8) features.
Continue reading “Upgrading to FreeBSD 13.0”FreeBSD 13.0 – Full Desktop Experience
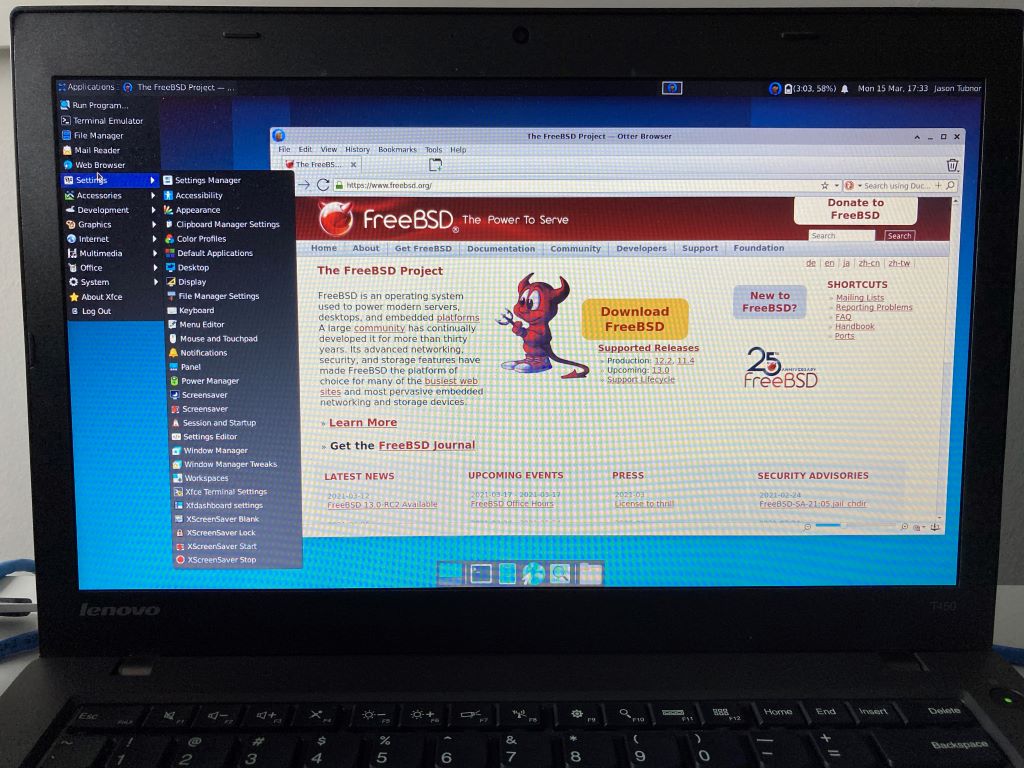
By: Jason Tubnor @tubsta
With the release of FreeBSD 13.0 on the horizon, I wanted to see how it shapes up on my Lenovo T450 laptop. Previous major releases on this laptop, using it as a workstation, felt very rough around the edges but with 13, it feels like the developers got it right.
I like to keep things simple when it comes to a desktop operating system so the description below is how I went from a fresh install of FreeBSD 13.0RC1 to a working environment that is based on using the XFCE4 desktop experience.
Continue reading “FreeBSD 13.0 – Full Desktop Experience”Creating a Chroot in OpenBSD
Foreword
This article describing the practical use of chroot on OpenBSD was originally written by Karsten Pedersen on 20 July 2014 and was located here until the IBM developerWorks connections platform was sunset at 2 January 2020. It has been kept in its entirety to help others that may have stumbled on an old Google search result.
Introduction
Chroots have many uses in UNIX-like operating systems and the chroot(8) command is not unique to OpenBSD. They are often used for security reasons in order to run a potentially vulnerable service in its own environment so that if it becomes compromised and an attacker manages to escalate their privileges to that of the compromised service, they are still constrained to the chroot that the service has been run in.
Continue reading “Creating a Chroot in OpenBSD”Camera SD card under OpenBSD
As file sizes increasingly become bigger in cameras such as Go Pro and Canon EOS D, the FAT file system has become unfit for purpose. As such, instead of looking to an open source file system (probably due to no support in the Windows or Mac platforms), these camera manufacturers have just done a bump to a more recent version of a Microsoft proprietary file system, exFAT. Continue reading “Camera SD card under OpenBSD”
OpenBSD and SNMPd
OpenBSD comes with a SNMP v2c and v3 daemon in base. Simplistic and privileged separated, this SNMP service is easy to configure and secure – putting Simple, backing into Simple Network Management Protocol (SNMP).
Recently, I have needed to flick on snmpd(8) to provide data to the Cacti logging service. The default configuration in /etc/examples/snmpd.conf will get most people going while only letting the daemon listen on the localhost interface, keeping your SNMP service reasonably secure. Continue reading “OpenBSD and SNMPd”
Reliable Bare Metal Server using TrueOS/FreeBSD
I currently have a project need for a simple FreeBSD base install that is hooked up to a NAS/SAN back end. Coming from a Solaris background, most SPARC machines (like the V220/V420) came rack mountable and space for 2 primary hard drives simply for the OS. You would spin up your OS install, install Solstice DiskSuite (Solaris Volume Manager), apply your secret sauce of configuration and you were away. One disk could fail and you could either hot swap replace and resilver or power down, boot off the disk that was functioning and then resilver to bring the new disk online (yes, I know there are more steps than this but that is out of scope for this article).
I wanted a similar, modern day solution like this, using commodity hardware and a free, open source and liberally licensed operating system.
While FreeBSD 10.x has a stable, binary update method for maintaining production machines, this doesn’t allow you to follow –HEAD to get the latest technology for the project that you are working on. The reason that I use OpenBSD so much in production, apart from the security aspect, is that you don’t have to wait long for new technology to appear in –release. This is why I think FreeBSD –HEAD is more suitable for my needs. Continue reading “Reliable Bare Metal Server using TrueOS/FreeBSD”